What is UAC?
What is UAC, you say? You’re in the right place! UAC, or user account control, is a security measure for Windows put in place to keep users safe. Try thinking of it as a checkpoint or barrier with a guard who asks you where you’re going and why you need access. It focuses on the premise of least privilege, which provides users with the tools they need to do their jobs and nothing more or less.
Whenever an application tries to make an administrative change on your device, UAC will have a notification pop up, warning you and asking you if you want to give permission or not. If you deny it, that application cannot proceed further; if you accept it, then you give permission for that application to complete its task.

Why is this important?
Malicious applications called malware want to gain access to your devices. Why does this matter? It gives bad actors a foothold into your system so they can do whatever they please, ranging from stealing information, changing your credentials, and even remotely taking over your system! An example of remote takeovers is ransomware, where a bad actor can lock your computer, encrypt your files, and demand payment or else your files will be deleted or released all over the internet.
Let’s Get Started
We’re going to do a surface dive into UAC and do an introduction, which will get you familiar with what UAC is, what it looks like, and what it does. You’ll then be prepared to customize your options to achieve your security goals.

Where the Magic Happens
This is the UAC console, which is where we’ll be exploring our customization options and where you’ll see the visual GUI of what UAC does. There’s a slider bar which allows you to either scroll up or down, and each option will show what enforcement level it provides, ranging from none to maximum security.
Anarchy Reigns
The first option that we have is the ability to turn off UAC completely and turn off notifications. This will disable notifications for when you make changes to Windows, and it’ll also not warn you about programs that make administrative changes and modifications to your computer. It’s the equivalent of having the wild west on your computer, and anything goes. This option is very unsafe, and I do not recommend it at all because it disables security for your computer. It’s the equivalent of a hacker’s paradise, and it lets them do whatever they want.
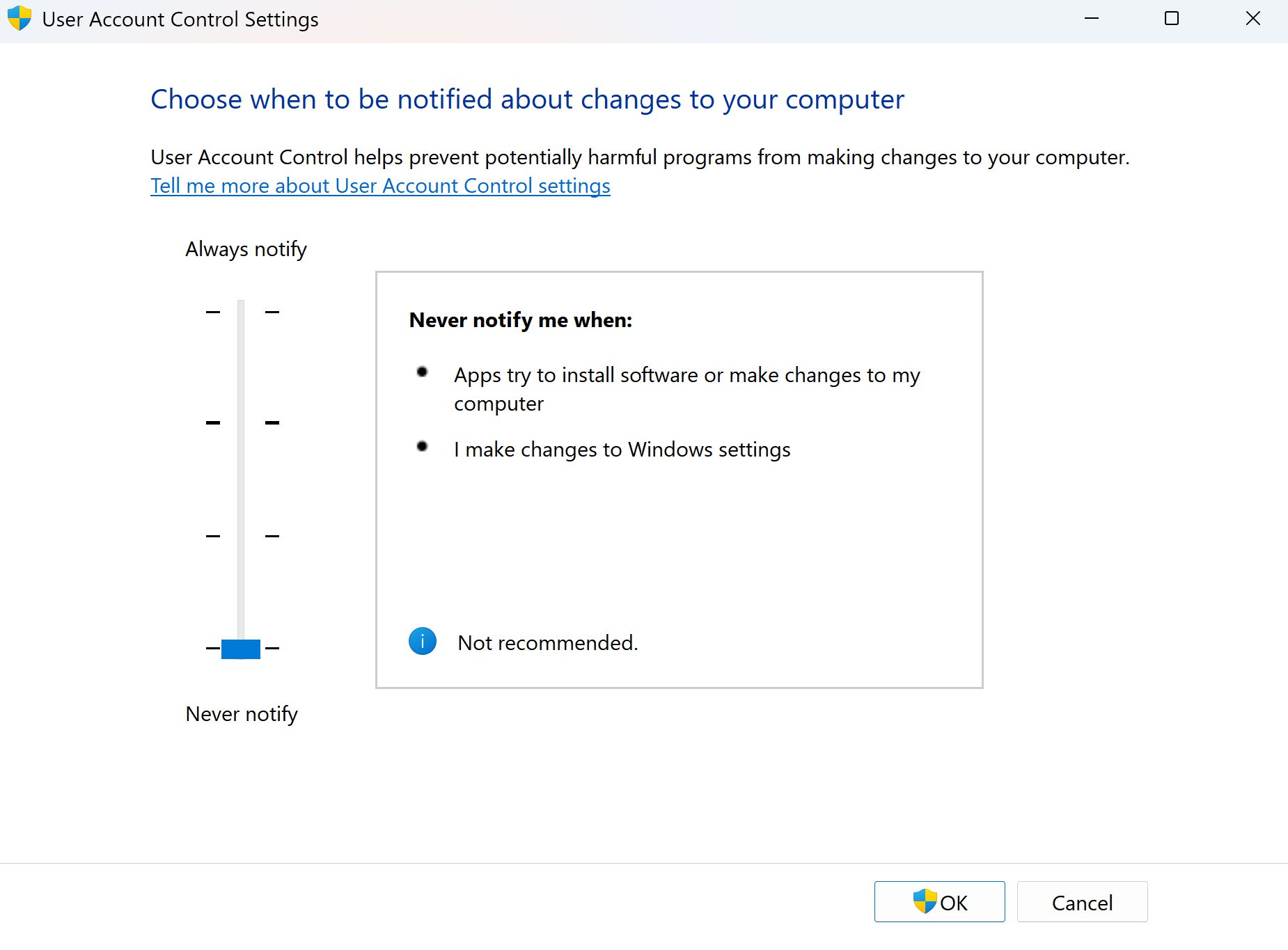
Think of it as sitting in a house that’s burning down around you or a frog sitting in a pot with boiling water that gets hotter and hotter. The meme below portrays exactly my point!

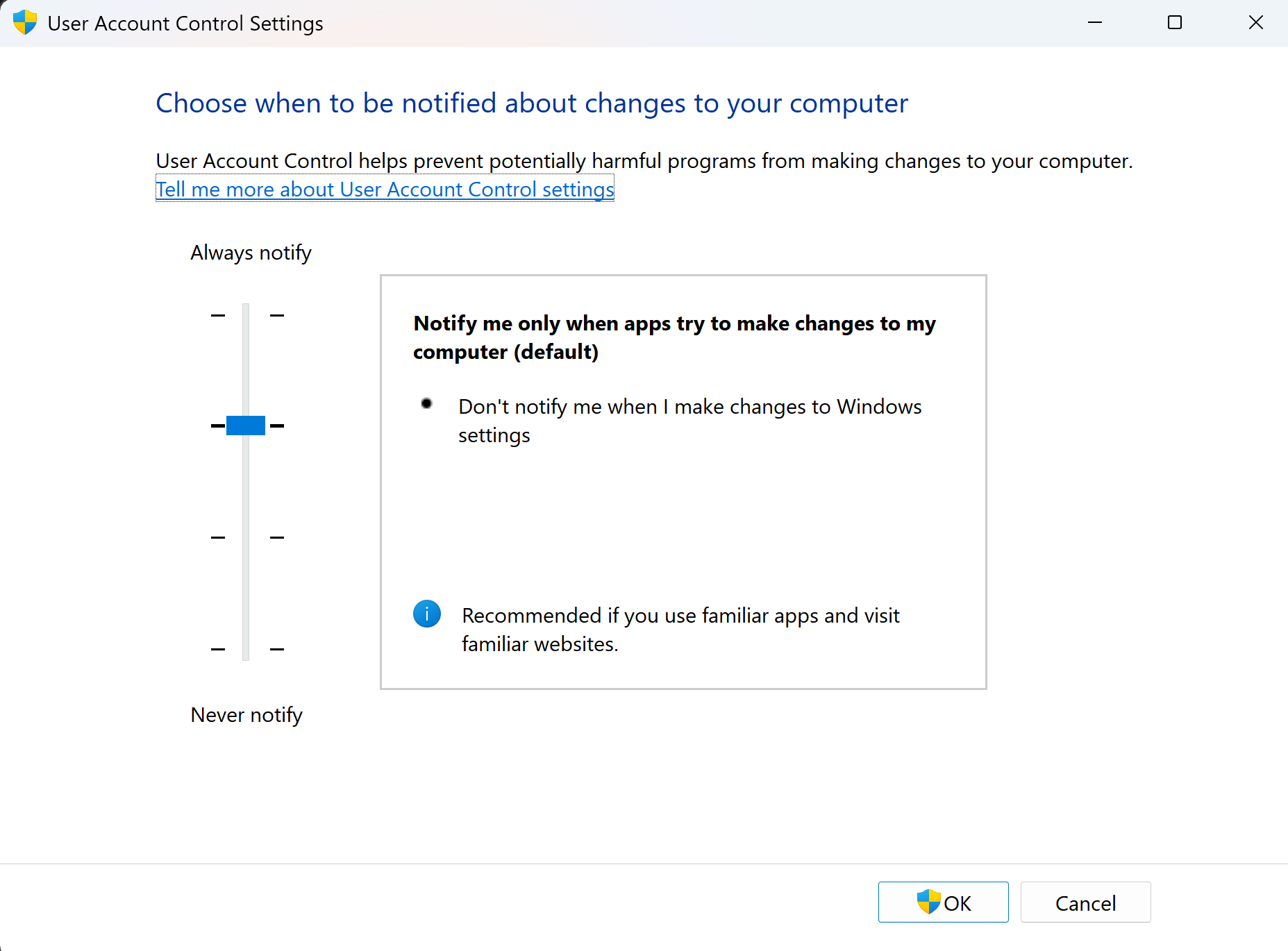
Keep the Lights On
The next option is a bit more secure, but it won’t warn you if you personally make changes to Windows. However, it’ll warn you if applications try to make changes to your device and that’s a step up in security from the previous choice we reviewed. Windows will also not dim your screen to warn you of a potential alert, and the lights will stay on. In normal settings, Windows will dim your screen to give a sense of urgency to the alert.
It’s not ideal, but it provides more security than not having any at all. You have to do your due diligence, as whatever you click on and change in Windows will not pop up as an alert. This puts all the liability on you because attackers still have a high chance of sneaking in if you’re not paying attention.
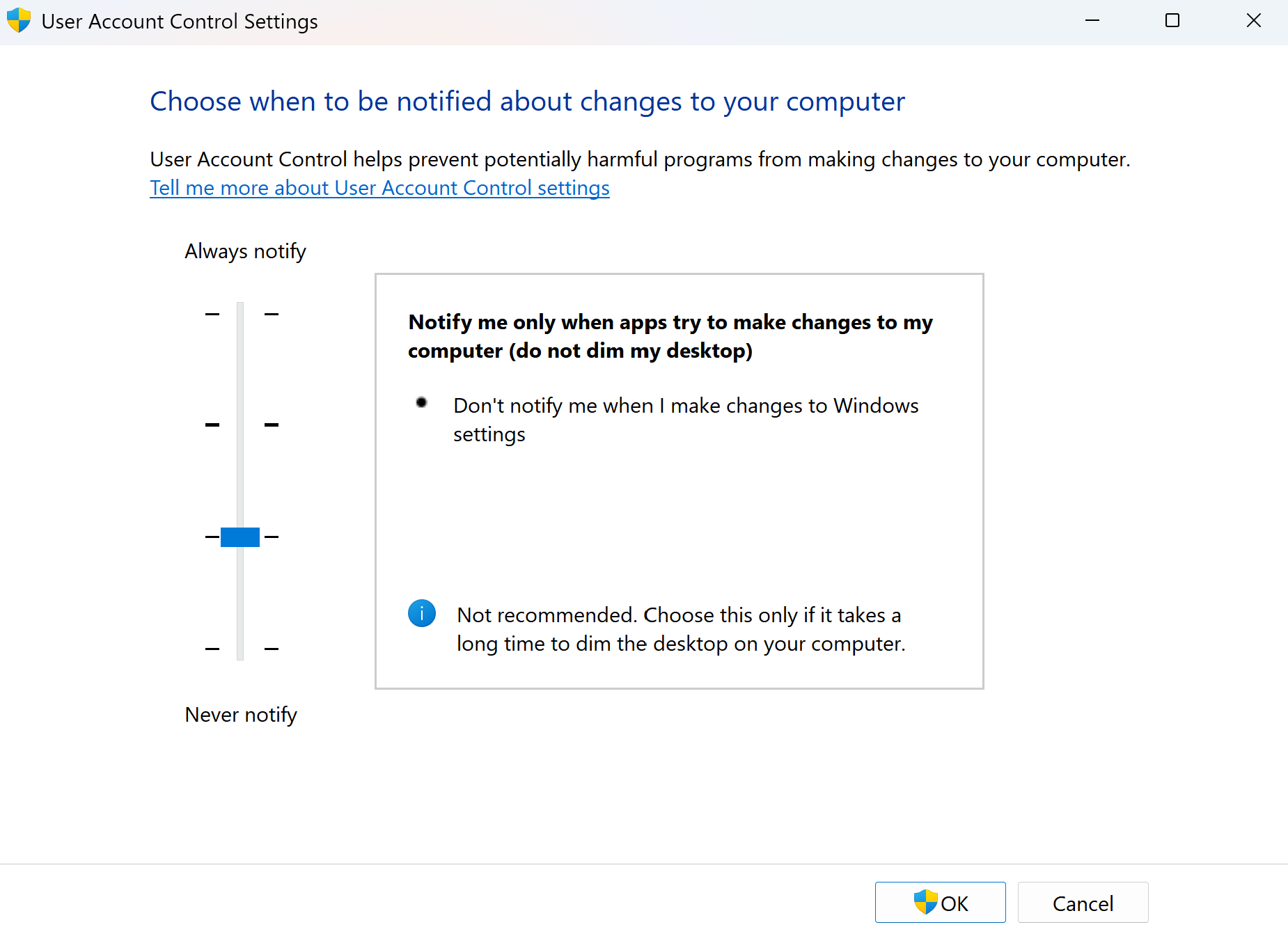
Recommended
The next option is the default option or recommended security settings for UAC. It’ll dim your screen on alert and warn you of applications trying to make modifications to your system. However, it won’t warn you if you make changes to Windows on your own. This is a more secure posture, as now the screen will dim on alert, and you’ll have to put your full attention on the alert. Attackers will now have to face you head-on if they want to get into your castle.
With this security posture, attackers will try their best to get in, but they’re limited in what they can do if you’re paying attention. They’ll depend on you making mistakes and allowing them in and they’ll try their hardest to find that chink in your armor.

King of the Castle
The last option that we’ll review is the most secure. It’ll warn you if anyone tries to make changes or install software on your device. It’ll also dim your screen and warn you if you make any changes to Windows. This security posture is the most secure, as you’ll be warned of anything that happens on your device. The only downside to this is that it may get annoying with the number of notifications and pop-ups that you’ll get. In my eyes, though, it’s a worthwhile sacrifice because you’re doing everything you can to keep your device safe.
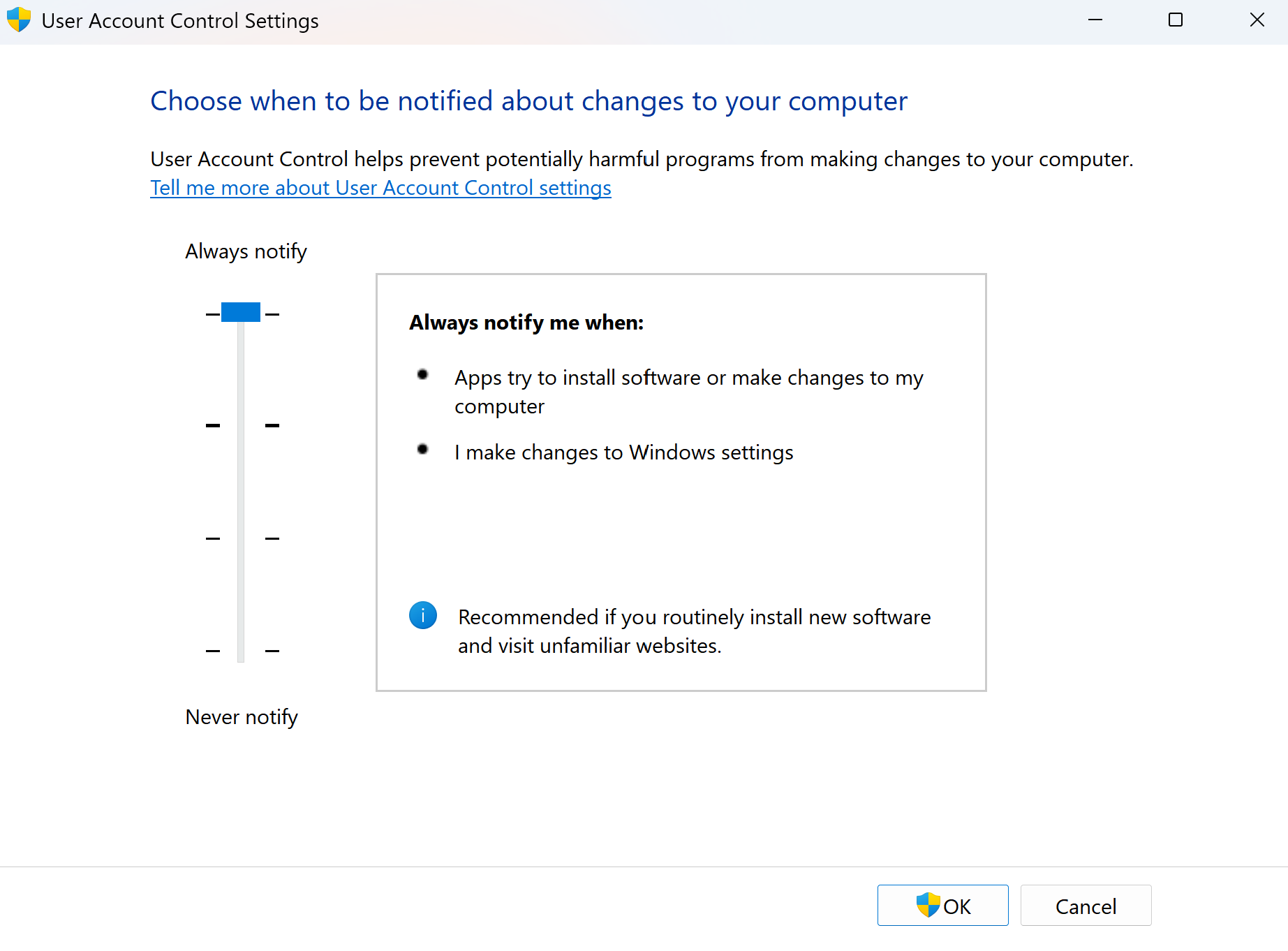
With this option, it’ll be very difficult for attackers to find a way in, and it’s the equivalent of them trying to scale a wall with barbed wire on top. Your computer will be secure, and it’ll be very difficult for them to get a foothold. However, this doesn’t eliminate the need for you to pay attention and be wary of what you install or click on.

The Adventure Concludes
Our adventure has come to an end and we’ve gone through the various options that UAC provides in terms of protection. Ranging from no protection at all to having the equivalent of a castle. UAC is an important security feature that will keep you safe when you’re surfing the internet and keep those pesky hackers away from your sensitive information. Do your due diligence and pick the option that works best for you, and remember to never let your guard down because the moment that you make a mistake, someone will be there to take advantage of it.